What is Cisco Meraki IPSK?
IPSK creates unique pre-shared keys for individuals or groups of users on the same SSID. It allows for the flexibility of using the same SSID for everything PSK related while still having different keys and policies on the network.
Here is a simple demo that shows how to configure IPSK with RADIUS using Identity Service Engine (ISE).
https://youtu.be/deEv-aNXfL0
Why IPSK?
WPA2-Enterprise with 802.1X authentication is commonly used for many enterprises, whereas home users use WPA/WPA2 Personal (aka WPA-PSK). Not all of these devices support 802.1x supplicant, so the enterprises need an alternative solution to connect the devices, such as IoT, sensors, BYOD, guests, etc. WPA-PSK could be considered an alternative, but the pre-shared key is the same for all clients connecting to the same WLAN. However, it may result in the key being shared with unauthorized users resulting in a security breach.
IPSK resolves these issues by allowing the flexibility to assign AAA override attributes such as VLAN, QoS marking, and ACL, which are normally reserved for 802.1X WLANs.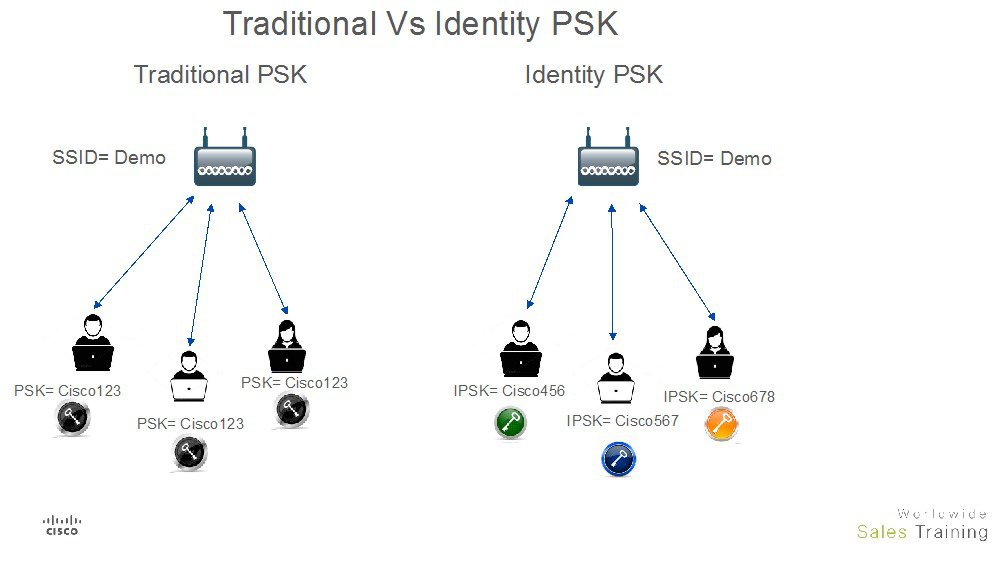
How to configure IPSK?
Please refer to the following sites.
Cisco Identify PSK - What is it, and how is it configured?
Implementing Cisco iPSK with ISE – Ripples in Harmony
No comments:
Post a Comment